 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
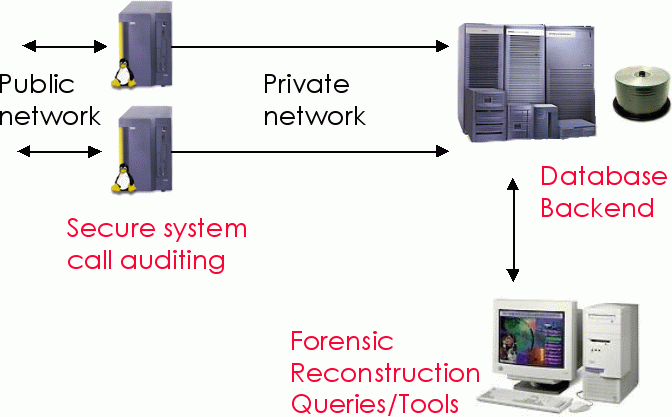
| The goal of the Forensix ("4N6")
Project is to allow a system to be monitored so that, in the event
of a security compromise, it is easy to track the compromise back to
its source. To facilitate this, the system requires two machines: a
potentially insecure "front-line" machine, and a known secure
back-end. Information about system calls is stored in a MySQL
database on the back-end. 4N6 is built on top of SNARE. | ||||||
 | ||||||
| ||||||
| The brunt of our research is covered
in the Hacking Fundamental slides; the link and instructions on
accessing the slides has been supplied above. Forensix is a high performance reconstruction and analysis tool for supporting computer forensics activities. It uses three main ideas to improve the accuracy and reduce the human overhead of performing forensic analysis; it performs comprehensive monitoring of the execution of a target system at the system call level, it streams the system-call information, in real-time, to append only storage on a separate, hardened, logging machine, and it uses database technology to support high-level querying of the archived log. What this means to the layman is that Forensix will record instances of intrusion, storing the attack information on a separate machine. This enables the network administrator the ability to research such attacks and secure the system against future intrusions. The ability to query, specifically, to query in a very detailed manner, gives the user a great deal of control in dealing with the mass amounts of information that the Forensix system records. |